Why is it necessary for the key (A) in the Affine Cipher to be coprime with the modulus 26, and what are the implications if it is not?
The Affine Cipher is a type of monoalphabetic substitution cipher that utilizes mathematical operations to encrypt and decrypt messages. The encryption process in the Affine Cipher involves two keys, typically denoted as ![]() and
and ![]() , and follows the formula:
, and follows the formula:
![]()
where ![]() represents the encrypted letter,
represents the encrypted letter, ![]() is the numerical equivalent of the plaintext letter (with
is the numerical equivalent of the plaintext letter (with ![]() ),
), ![]() and
and ![]() are keys, and 26 is the modulus, corresponding to the number of letters in the English alphabet.
are keys, and 26 is the modulus, corresponding to the number of letters in the English alphabet.
For decryption, the formula used is:
![]()
where ![]() represents the decrypted letter,
represents the decrypted letter, ![]() is the numerical equivalent of the ciphertext letter, and
is the numerical equivalent of the ciphertext letter, and ![]() is the modular multiplicative inverse of
is the modular multiplicative inverse of ![]() modulo 26.
modulo 26.
The necessity for the key ![]() to be coprime with the modulus 26 stems from the requirement to find the modular multiplicative inverse of
to be coprime with the modulus 26 stems from the requirement to find the modular multiplicative inverse of ![]() during the decryption process. A number
during the decryption process. A number ![]() is said to be coprime (or relatively prime) with another number
is said to be coprime (or relatively prime) with another number ![]() if their greatest common divisor (GCD) is 1, i.e.,
if their greatest common divisor (GCD) is 1, i.e., ![]() .
.
Why Key 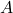 Must Be Coprime with 26
Must Be Coprime with 26
1. Existence of Modular Inverse:
The modular multiplicative inverse of ![]() modulo 26 exists if and only if
modulo 26 exists if and only if ![]() and 26 are coprime. The modular inverse
and 26 are coprime. The modular inverse ![]() is a number such that:
is a number such that:
![]()
If ![]() is not coprime with 26, the equation above has no solution, meaning
is not coprime with 26, the equation above has no solution, meaning ![]() does not exist. Without the inverse, the decryption formula cannot be applied, rendering the decryption process infeasible.
does not exist. Without the inverse, the decryption formula cannot be applied, rendering the decryption process infeasible.
2. Ensuring Unique Decryption:
When ![]() and 26 are coprime, each ciphertext letter maps uniquely to one plaintext letter. If
and 26 are coprime, each ciphertext letter maps uniquely to one plaintext letter. If ![]() is not coprime with 26, the mapping between plaintext and ciphertext is not bijective, leading to multiple plaintext letters potentially mapping to the same ciphertext letter. This ambiguity undermines the cipher's reliability and security.
is not coprime with 26, the mapping between plaintext and ciphertext is not bijective, leading to multiple plaintext letters potentially mapping to the same ciphertext letter. This ambiguity undermines the cipher's reliability and security.
3. Mathematical Properties:
The coprimality condition ensures that the linear transformation applied by the Affine Cipher is invertible. The mathematical foundation of the Affine Cipher relies on linear algebra principles, where invertibility is important for reversing the transformation.
Implications if 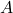 is not Coprime with 26
is not Coprime with 26
1. Non-existence of Inverse:
If ![]() is not coprime with 26, the modular inverse
is not coprime with 26, the modular inverse ![]() does not exist. For example, if
does not exist. For example, if ![]() , which shares a common factor of 13 with 26, there is no integer
, which shares a common factor of 13 with 26, there is no integer ![]() such that:
such that:
![]()
Consequently, it is impossible to decrypt the ciphertext using the standard decryption formula.
2. Ambiguity in Decryption:
Suppose ![]() , which is not coprime with 26 (since
, which is not coprime with 26 (since ![]() ). In this case, the mapping is not one-to-one. For instance, both plaintext letters 'a' (
). In this case, the mapping is not one-to-one. For instance, both plaintext letters 'a' (![]() ) and 'n' (
) and 'n' (![]() ) would map to the same ciphertext letter:
) would map to the same ciphertext letter:
![]()
![]()
This results in a ciphertext where multiple plaintext letters correspond to the same ciphertext letter, creating ambiguity and making it impossible to uniquely determine the original plaintext.
3. Security Weakness:
The security of the Affine Cipher relies on the difficulty of deducing the keys from the ciphertext. If ![]() is not coprime with 26, the cipher becomes more predictable and easier to break. The redundancy introduced by non-coprime
is not coprime with 26, the cipher becomes more predictable and easier to break. The redundancy introduced by non-coprime ![]() values reduces the effective key space, making the cipher more vulnerable to cryptanalysis.
values reduces the effective key space, making the cipher more vulnerable to cryptanalysis.
Example of Valid and Invalid Keys
– Valid Key Example:
Let ![]() and
and ![]() .
.
Since ![]() ,
, ![]() is coprime with 26. The encryption function is:
is coprime with 26. The encryption function is:
![]()
To decrypt, we need the modular inverse of 5 modulo 26. Using the Extended Euclidean Algorithm, we find that ![]() . The decryption function is:
. The decryption function is:
![]()
This ensures that each ciphertext letter can be uniquely decrypted to its corresponding plaintext letter.
– Invalid Key Example:
Let ![]() and
and ![]() .
.
Since ![]() ,
, ![]() is not coprime with 26. The encryption function is:
is not coprime with 26. The encryption function is:
![]()
Attempting to decrypt, we find that 6 does not have a modular inverse modulo 26. Therefore, the decryption process cannot be performed using the standard formula, leading to an unusable cipher.
Conclusion
The requirement for the key ![]() in the Affine Cipher to be coprime with the modulus 26 is fundamental to the cipher's functionality. It ensures the existence of a modular inverse, which is essential for the decryption process. Without this condition, the cipher fails to provide a unique and reversible mapping between plaintext and ciphertext, compromising both the usability and security of the encryption scheme.
in the Affine Cipher to be coprime with the modulus 26 is fundamental to the cipher's functionality. It ensures the existence of a modular inverse, which is essential for the decryption process. Without this condition, the cipher fails to provide a unique and reversible mapping between plaintext and ciphertext, compromising both the usability and security of the encryption scheme.
Other recent questions and answers regarding EITC/IS/CCF Classical Cryptography Fundamentals:
- Is cryptography considered a part of cryptology and cryptanalysis?
- Will a shift cipher with a key equal to 4 replace the letter d with the letter h in ciphertext?
- Does the ECB mode breaks large input plaintext into subsequent blocks
- Do identical plaintext map to identical cipher text of a letter frequency analysis attact against a substitution cipher
- What is EEA ?
- Are brute force attack always an exhausive key search?
- In RSA cipher, does Alice need Bob’s public key to encrypt a message to Bob?
- Can we use a block cipher to build a hash function or MAC?
- What are initialization vectors?
- How many part does a public and private key has in RSA cipher
View more questions and answers in EITC/IS/CCF Classical Cryptography Fundamentals

